23 Oct Cybersecurity Plan
Cybersecurity 2021
Cybersecurity: a key point in industry 4.0
Applying improvements and implementing new measures that affect cybersecurity has become one of our main priorities. Why? These are the reasons:
- We want to continue making progress in our industry 4.0 plan, which includes advancing in the digitization of all our production processes, and therefore developing new computer systems, as well as improving and securing the ones we already have.
- One of our corporate objectives is security –in computer systems as well– and consequently the security of our information and that of our partners: customers, suppliers, workers, etc. We want to protect ourselves against hackers and new forms of cyber-attacks.
The security of all the information handled by our company is an aspect of primary importance for Rieusset. Let’s find out what our situation is in this regard with the Personnel Director and coordinator of the cybersecurity project, Pilar Pintor, and also with the company contracted for the execution of the plan, Ingram Cloud Cyber Security.
Cybersecurity audit
In May 2021, the German company Ingram Cloud Cyber Security was hired to begin the audit process that could facilitate the starting point of our company in terms of cybersecurity. The objective was to uncover any vulnerabilities in our computer systems that could put our activity or the protection of sensitive data at risk.
Ingram Cloud Cyber Security carried out different activities to determine what vulnerabilities Rieusset had in terms of cybersecurity, verifying these and determining the security risk level associated with the environment and its corresponding assets in order to establish an action plan to mitigate them.
To do this, they carry out two types of interventions:
- The external one, which consists of trying to enter and attack our computer system from outside, as if it were a hacker.
- The internal one, carried out from inside the company as if it were an internal person with access to staff computers, servers, etc.
Each of these interventions is carried out in the following phases:
- Planning phase. Identification of the rules, scope of the test, access points to verify, timing and objectives.
- Discovery phase. Automated vulnerability scanning using industry standard tools.
- Once the vulnerabilities are identified, they are verified and classified according to the likelihood and risk they pose to Rieusset.
- Final phase. Recording of all findings, risk assessment and steps to follow in order to mitigate it. Finally everything is compiled in a report.
Tests and results. Cybersecurity audit
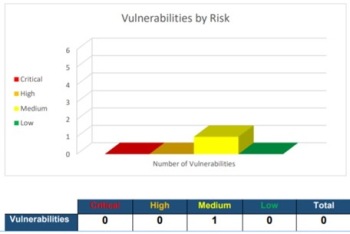
Let’s start with the external test.
As can be seen in the graph, the results were very positive, as only one medium risk vulnerability was found, which the report determines as: moderate security problems that require some effort to successfully influence the environment. The report also explains that at the time of the test they found themselves up against a well-reinforced external perimeter that made it impossible to finish the attack successfully.
To date, the detected incident has already been worked on and solved, thus achieving maximum security in our system against external attacks.
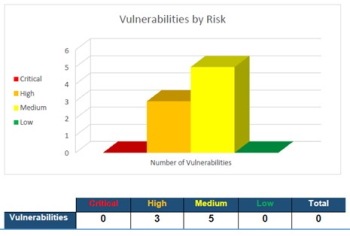
Let’s also have a look at the internal test.
As can be seen in the graph, the number of vulnerabilities was still very low and most of them carried a medium risk (as in the external test). Although there were certain situations from which it was possible to attack the system, the attacks were unsuccessful because we had internal systems reinforced with firewalls, antivirus or network intrusion detection systems.
As indicated by Pilar Pintor, the coordinator of the cybersecurity project: “in this regard, we felt reassured knowing that many actions we were taking to date were correct and truly protected us.”
Even so, we worked on all the vulnerable points until we managed to solve them. To date, all the weak points have been reinforced and we now have a much more secure computer system.
Cybersecurity 2022
Although all the vulnerabilities have been corrected, we plan to carry out more tests periodically to continue guaranteeing the security not only of our company, but also of our workers, customers, suppliers and all our interested parties.
As explained by our cybersecurity coordinator, Pilar Pintor: “internally, for example, we have carried out (and will continue to do so) training with cybersecurity specialists for our office staff. In this way, they will be well informed and will know how to act.”
One of the latest developments is the incorporation last December of a computer technician, Alejandro Beltrán, whereby we strengthen our IT area in all its aspects, having more resources to continue working on our cybersecurity.
In 2022, our objective is to continue working to be a healthy, sustainable and safe company, which also includes being cybersecure.
Cybersecurity audit 2022
Continuing on our path towards Industry 4.0, cybersecurity is always one of our corporate purposes. For this reason, we wanted to repeat the audit with Ingram Cloud Cyber Security, a company specialized in cybersecurity for companies with which we started working in 2021.
In this audit, external and internal intrusion tests were performed. Let’s have a look at the results obtained:
– In the external intrusion tests of the audit, the results were very positive. A slight risk vulnerability was detected in one of our applications, although upon contacting our supplier of that application, we found that they were already aware of it and a security patch has been applied to correct it.
– In the internal intrusion tests, posing as company personnel, i.e. a person from inside the company with access to staff computers, servers, etc., some medium and slight vulnerabilities were detected. We are already correcting them, although they do not affect the security of the company, thanks to having a well-reinforced system that makes it impossible to complete a successful attack.
Cybersecurity 2022
During 2022 we made important changes to continue improving the company’s cybersecurity, since this world is in a state of permanent development. Among the changes that were made, these are the most significant:
– Separating the net into sections. This makes it possible to mitigate any possible damage or intrusions and even isolate certain elements to prevent any threat from spreading.
– Updating firewalls. These are computer elements that control the traffic of a device or a private network to block the entry of threats. This change in hardware helps us to monitor and apply new guidelines to the network and thus reinforce it and have a much safer computer system which above all is updated against new threats.
In addition, we have taken a step towards integrated cybersecurity for the entire Gerosa Group by implementing a new module in the security project we initiated for the entire group, called “MDR” (Manager Detection & Response). Thanks to the fact that all the companies forming part of the Gerosa Group have implemented the same Sophos firewalls at the security level, we have easier conditions for implementing this important service, which provides us with proactive monitoring and management in case of incidents on our devices with 24/7 coverage.
This means having a true outsourced SoC (Security Operations Center) service, with highly specialized teams that are dedicated to just that, backed by the Sophos guarantee of expertise.
Cybersecurity 2023
Internally, we continue to carry out (and will continue to do so) training with cybersecurity specialists for our personnel. In this way, we can show them what could happen in different scenarios, as well as the new methods of phishing, malware or viruses, so that they know how to act and become aware that it is a very important point to take into account for the security of the company.

| We Manufacture: | Meet Rieusset: |